NightSpire Ransomware Analysis

Overview of the NightSpire Ransomware Group
NightSpire is a ransomware group first discovered in the wild in March 2025. Within just 6 months, the group has captured the attention of global cybersecurity analysts and claimed over 73 victims worldwide. The group blends traditional ransomware tactics with aggressive public shaming and precision targeting, making them a formidable threat.
NightSpire employs a double extortion strategy. They not only encrypt their victims' systems but also threaten to publish the stolen data on their onion-based Data Leak Site (DLS), which went live on March 12, 2025.

Infection Chain
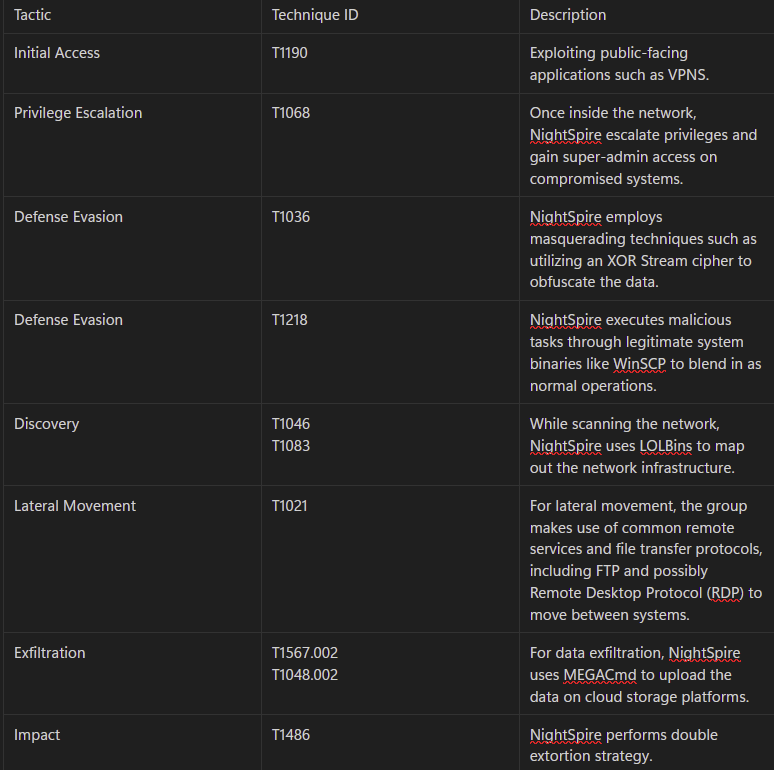
- The group exploits vulnerabilities in corporate networks to gain initial access, primarily targeting outdated VPN appliances and unpatched Remote Desktop Protocol (RDP) services.
- After compromising the machine, the group relies on a combination of legitimate system tools and stealthy execution tactics to stay under the radar. Their toolkit includes WinSCP, MEGACmd, 7-Zip, and Everything.exe, all legitimate programs repurposed for malicious intent. NightSpire will then uses these tools to scan connected file shares and databases to identify high-value assets within the network.
- Once NightSpire collects the necessary information, they initiate the encryption process, targeting all files within the victim's network.
- Upon completion of encryption, victims find their files with the ".nspire" extension and a ransom note named "readme.txt" placed in each compromised directory.
Victimology
Since its discovery approximately 50 days ago, the group has already compromised 73 victims across the following countries:
- United States
- Mexico
- Canada
- Costa Rica
- Venezuela
- Ecuador
- Peru
- Brazil
- Chile
- Argentina
- Portugal
- Spain
- France
- United Kingdom
- Sweden
- Norway
- Italy
- Germany
- Poland
- Czech Republic
- Austria
- Turkey
- Egypt
- United Republic of Tanzania
- South Africa
- India
- Thailand
- Malaysia
- Indonesia
- Philippines
- South Korea
When visiting NightSpire's site, they have a "Databases" section that displays victim information. This section includes company names, breach dates, data sizes, and countdown timers indicating when public disclosure of stolen data will occur.
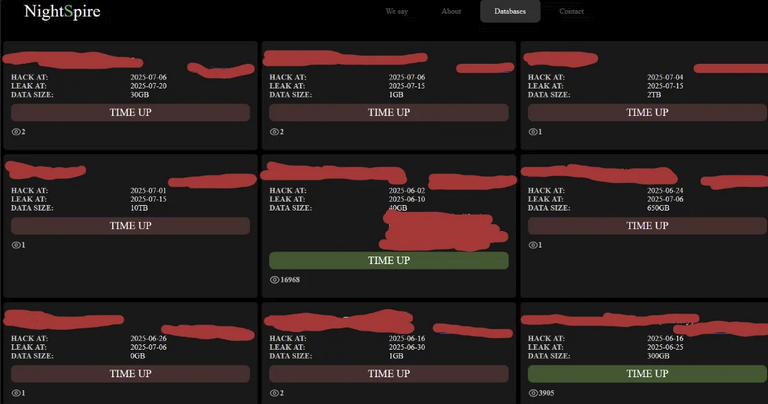
To date, the NightSpire ransomware group has targeted victims across diverse sectors including healthcare, education, automotive, manufacturing, government and law enforcement, construction, technology, retail, and logistics.
NightSpire Infrastructure
NightSpire uses multiple encrypted platforms for ransom negotiations, including ProtonMail, OnionMail, and Telegram. Their "Contact Us" page provides four communication channels: onion mail, Telegram, Tox chat, and Session. Each victim is assigned a unique ID in their ransom note, allowing NightSpire to track infections individually.

File Analysis
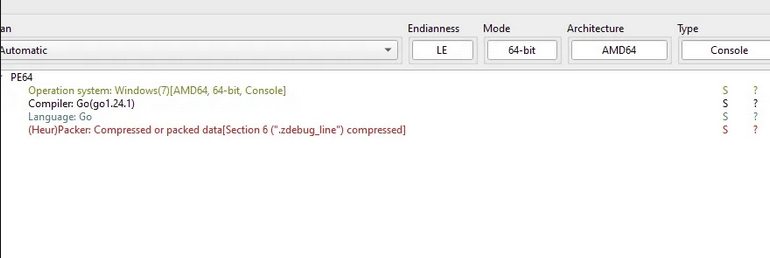
Analysis using Detect It Easy (DIE) showed that the malware is a Win32 executable written in Go programming language. The sample was compiled with Go compiler version 1.24.1. DIE also identified compressed data within section 6 of the PE header file.
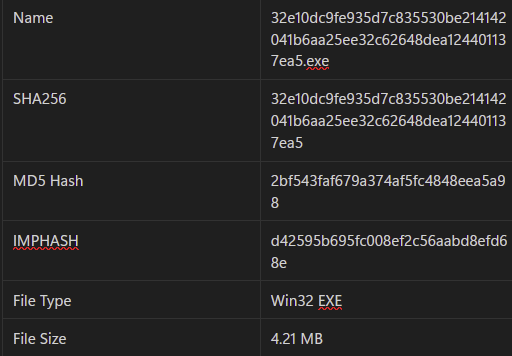
Entropy
Analysis of the file's entropy shows that 87 percent is packed. Examining each section of the PE header reveals the following obfuscated sections:
- section (2) [’.data’]
- section (6) [’.zdebug_line’]
- section (7) [’.zdebug_frame’]
- section (9) [’.zdebug_info’]
- section (10) [’.zdebug_loc’]
- section (11) [’.zdebug_ranges’]
This strongly indicates that the file has been deliberately modified to obfuscate data and evade static detection methods.
Strings
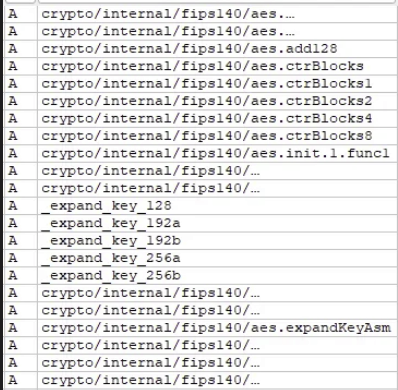
Numerous unique strings were discovered displaying ransom like behavior below.
Encryption
NightSpire employs a hybrid cryptographic approach that combines symmetric encryption (AES) with asymmetric encryption (RSA). The ransomware uses AES with a 256-bit key to encrypt files—a standard practice in ransomware attacks. This AES encryption key is then itself encrypted using an RSA public key, while the attackers retain the private key necessary for decryption once the ransom has been paid.
In addition, I also see the malware uses XOR key stream to obfuscate the file and evade detection.
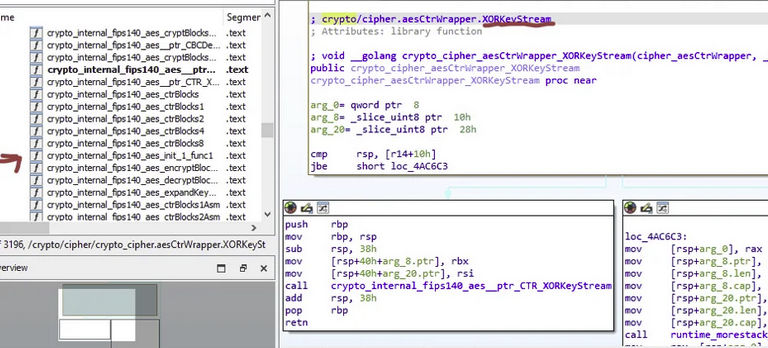
File Execution
Once the malware is executed, NightSpire's infection mechanism operates through a multi-stage loader that first disables Windows Defender and deletes volume shadow copies to prevent easy recovery. The loader then launches the Windows command prompt and enumerates accessible files and directories, excluding system-critical paths to avoid destabilizing the host.
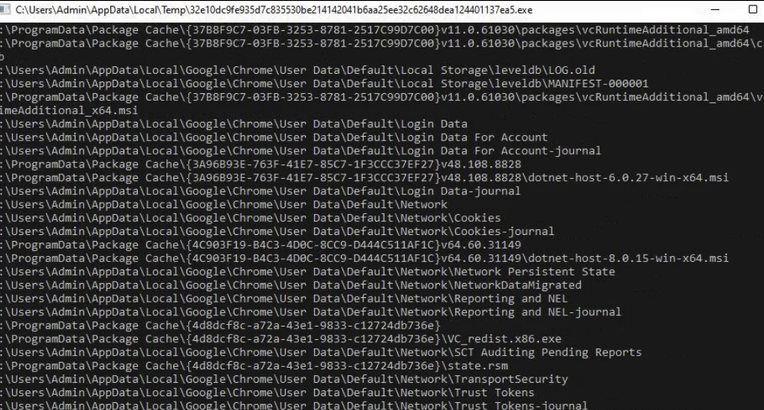
Once encryption is complete, all files on the victim's machine are encrypted, and a readme.txt ransom note appears on the desktop.
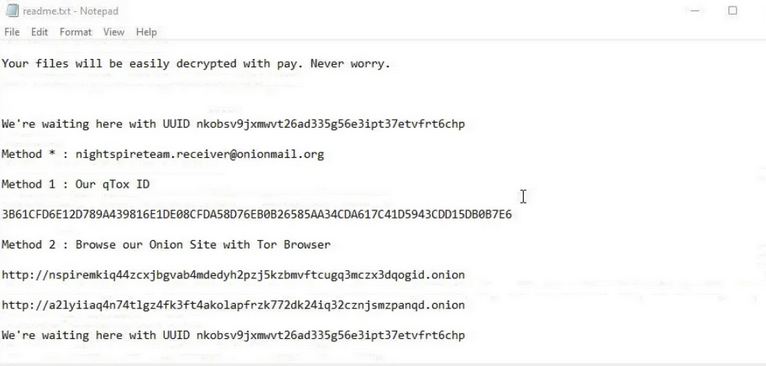
When opened, the ransom note declares that all servers and files have been locked, provides a unique UUID, and lists various contact methods for reaching the attackers.
Conclusion
NightSpire is a rapidly emerging threat group that has acquired 72 victims in just 50 days. Their operations range from pure data exfiltration to full-scale ransomware encryption. They have built a functioning leak site while operating in secrecy and continuously targeting new victims. Organizations must remain vigilant and adopt a proactive, intelligence-driven security strategy to defend against NightSpire.
Mitigation and Defense Strategies
- Timely Patch Management: Timely Patch Management: Ensure all systems, especially public-facing services like firewalls, VPNs, and email gateways, are regularly updated.
- Endpoint Detection and Response (EDR) Deployment: Deploy advanced EDR solutions with behavioral analysis and threat hunting capabilities. These tools can identify lateral movement, detect misuse of living-off-the-land binaries (LOLBins), and flag unauthorized execution of tools such as PowerShell, MEGACmd, and WinSCP.
- Network Segmentation and Access Controls: Use VLANs and strict firewall rules to separate critical infrastructure from less sensitive systems. This limits lateral movement and minimizes damage in case of a breach.
- Multi-Factor Authentication (MFA): Implement MFA across all endpoints, especially for privileged accounts and remote access solutions like RDP. This adds a vital security layer that remains effective even when credentials are compromised.
- Cloud and Data Exfiltration Monitoring: Monitor for unusual traffic to cloud storage services (e.g., MEGA), especially involving tools like MEGACmd. Block or restrict access to known exfiltration channels using proxy filters or data loss prevention (DLP) solutions.
Tactics Techniques and Procedures (TTPS)